When I’ve set up my Odroid Server earlier this year, I’ve wondered if it was a good idea to run a public-facing DNS resolver based on Pi-Hole. Against all the voices telling me no, I decided nonetheless to try it and see what happens. In the end, the traffic will be limited at some point by the CPU power available, and the Operations Team at CommunityRack.org will give me a hearty slap on the wrist saying, “you broke it, you’ll fix it”, and they will make me buy some Pizza and/or Doughnuts for the next time we meet in person. So the experiment began towards mid-February.
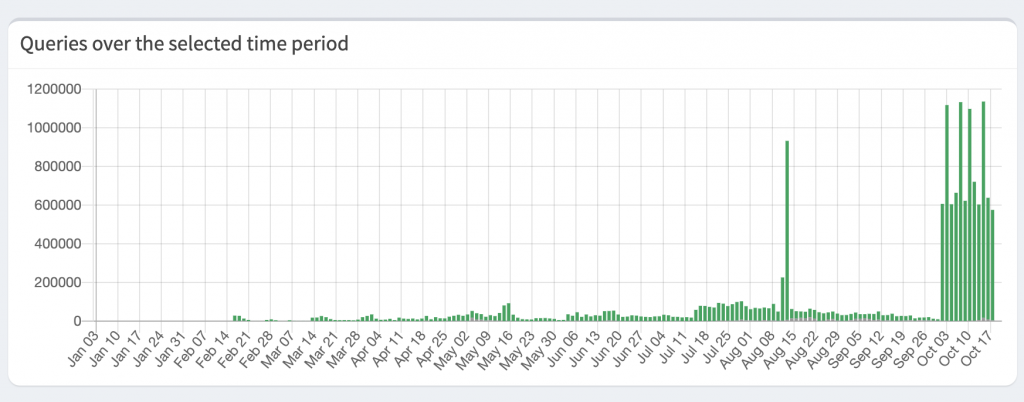
You can see the traffic I was making most of the time until around May. Primary clients connected to the VPN using the DNS Resolver following mostly standard day/night/weekend traffic patterns.
There’s a noticeable bump in July, a considerable Spike towards august, and then in October, the floodgates opened entirely with a couple of million DNS queries per day. My theory is that at some point in July, the resolver got on some well known DNS list and started to gain “trust” as it was always online.
A few observations:
- First, there was only my traffic, but soon after, someone or a small group of people discovered the resolver and started using it.
- Discovery — I was confused why and how people found the resolver, but they seemed to use it steadily.
- Service-Thoughts — But you can’t get in touch with someone like that, so I’ve set up a small landing page on the IP and added an email address for anyone to reach out if they plan to use the service for an extended time, so I could give them at least a heads up in case the service needs to shut down. If you ever debug a failing DNS server, you would know why – Nobody deserves this.
- Privacy — It was when I noticed that I’d need to shred the log files at some point and started lowering the data logged to disk. The less I know, the better. At this point, I only cared for the raw numbers.
- Trust? — And last and the most concerning one for me personally is that people seem to blindly trust a random IP on the internet that gives them DNS responses. (I kind of pride myself that I was able to run a DNS resolver with seemingly good uptime and minimal maintenance).
So how long?
The answer is 7 months and 3 days (15th March till 18th October).
Sorry to the people that have a broken DNS resolver now. And sorry if my resolver has been part of some sort of a DNS Amplification Attack (based on the traffic it should not have, but that’s hard to say).
The experiment has ended; thanks for participating. I’ve just shredded all logs.